https://edition.cnn.com/2020/07/15/tech/twitter-hack-elon-musk-bill-gates/index.html
Best Practices:
 |
| Info sourced from CNN News |
 |
| Info sourced from CNN News |
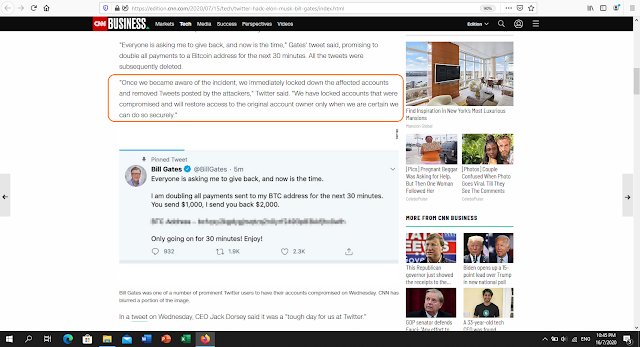
- Immediately locked down affected accounts
- Removed illegal posts
- Investigate and be transparent with users on the findings
Comments from Kaspersky:
Best practices Advice From Kaspersky:
“This major scam flags the fact that we are living in the era when even people with computer skills might be lured into scammers trap, and even the most secure accounts can be hacked. To our estimates, within just two hours at least 367 users have transferred around 120,000 dollars in total to attackers. Cybersecurity is undoubtedly one of the top priorities of all major social media platforms, and they put efforts in preventing many attacks every day. However, neither website nor software is entirely immune to bugs, nor is the human factor immune to mistakes. Therefore any native platforms might be compromised. Today we see how, along with new attack vectors, scams combine old and effective techniques, to use a surprise element and gain people’s trust to facilitate the attack and lure victims into a trap. For instance, it might be a mixture of supply chain attacks with social engineering. In addition, the threat actors might gain access to victim’s account in other ways: for instance, it can be penetrating a third-party app with access to the user’s profile, or users’ password might be brute-forced.
However, we urge everyone not to panic, and simply accept a new mind-set: the social media account users require a responsible approach and thorough protection, but we are not lambs to the slaughter. This incident might mean we all need to take some time to reassess our approach to our relationships with social media and accounts security, but once we do it, it will become evident that we possess knowledge and instruments to recognize even the most elaborate scam and minimize its impact,” – said Dmitry Bestuzhev, cybersecurity experts at Kaspersky.
However, we urge everyone not to panic, and simply accept a new mind-set: the social media account users require a responsible approach and thorough protection, but we are not lambs to the slaughter. This incident might mean we all need to take some time to reassess our approach to our relationships with social media and accounts security, but once we do it, it will become evident that we possess knowledge and instruments to recognize even the most elaborate scam and minimize its impact,” – said Dmitry Bestuzhev, cybersecurity experts at Kaspersky.
Best practices Advice From Kaspersky:
- While it is absolutely essential to have a strong password, it should also be unique, so that if other website leaks your credential, your accounts remain safe. To create safe and complicated password to each website, use memory techniques or a password manager.
- Use two-factor authentication, when login and password need to be confirmed by entering a special code. Furthermore, consider using not a text message to receive this code, as it can be hijacked, but an app that generates such codes. Alternatively, use a physical key, connected to the separate device through USB-cable or NFC.
- Another security measure that needs to be taken – is a thorough review of the apps that have access to the twitter account. They can be found in twitter account settings. We recommend revoking access to your account from all of them, or the ones that you don’t consider thoroughly protected so that in case of their hack your account can’t be reached.
- Start using https://privacy.kaspersky.com/ to help make your social media profiles more private. It will make it harder for third parties to find highly personal information.
Comments from Sophos:
- If a message sounds too good to be true, it IS too good to be true. If Musk, Gates, Apple, Biden or any well-known person or company wanted to hand out huge amounts of money on a whim, they wouldn’t demand that you hand them money first. That’s not a gift, it’s a trick, and it’s an obvious sign that the person’s account has been hacked. If in doubt, leave it out!
- Cryptocurrency transactions don’t have the legal protections that you get with banks or payment card companies. There is no fraud reporting service or transaction cancellation in the world of cryptocurrency. Sending someone cryptocoins is like handing over banknotes to in an envelope – if they go to a crook, you will never see them again. If in doubt, don’t send it out!
- Look out for any and all signs that a message might not be real. Crooks don’t have to make spelling mistakes or get important details wrong, but often they do; So if the crooks do make a blunder, such as writing 50$ when in your country the currency sign comes first, making a mess of their own phone number, or using clumsy or unnatural language, don’t let them get away with it. Treat it with doubt unless everything checks out!
- For more information, kindly refer to this Naked Security article.
Comments